Test for different scenarios - credential theft compromised machines and other security flaws. Ad The ultimate race and flight simulator for home and business.
 Breach And Attack Simulation Gartner Cool Vendor 2020
Breach And Attack Simulation Gartner Cool Vendor 2020
As organisations try and stay one step ahead of cyber criminals Breach and Attack Simulations BAS are growing in popularity as a way of testing cyber resilience.
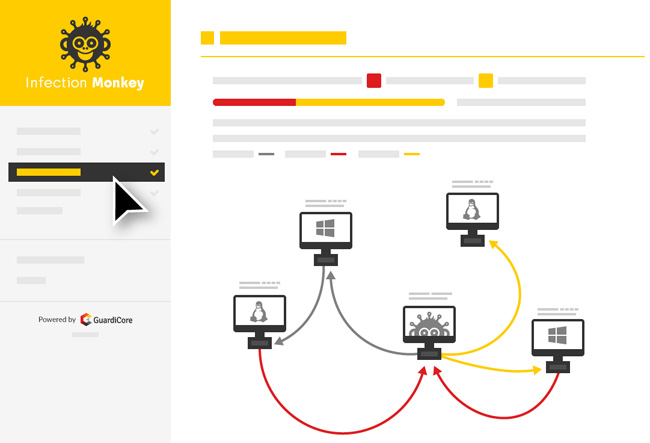
Breach and attack simulation. In fact there is much in common between BAS and Automated Penetration Testing. Breach Attack Simulation BAS is a new approach to attack simulation and differs from the traditional pentests and red teaming exercises in a significant way. But lets get back to the concept of Breach and Attack Simulation or BAS.
Breach Attack Simulation BAS platform that makes it simple to know and optimize your security posture any time all the time. Breach and attack simulation BAS software is used to mimic real-world security threats to help businesses prepare incident response plans and discover potential vulnerabilities in their security systems. By 2022 organizations that use the risk-based vulnerability management method will suffer 80 fewer breaches.
Although it may sound overly dramatic there is a veritable epidemic of misconfigured disconnected turned off and non-optimized security tools all over the. What is Breach and Attack Simulation. In this sense a breach and attack simulation acts much like a continuous automated penetration test and it improves upon.
These simulations can be carried out in an automated and continuous way mitigating to a certain extent the problem of the lack and cost of specialized personnel. Ad The ultimate race and flight simulator for home and business. The traditional tests are valuable in that they provide insights in the most probably attack path that an adversary may take.
It is a powerful approach since it allows you to. Breach and attack simulation or shortly BAS is a new security technology which allows to automatically find vulnerabilities in your infrastructure. Automated Breach and Attack Simulation Analysis Simply infect a random machine with the Infection Monkey and automatically discover your security risks.
The technology is used to automatically spot weaknesses in an organisations cyber security a little like automated ongoing penetration testing. There are three different types of BAS solutions. These simulated attacks might send fake phishing attacks to employees or attempt a cyberattack on a companys web application firewall.
We use SafeBreach inside Paypal to gain a continuous measureable and complete view of our security posture. Learn how your peers are benefiting from Breach and Attack Simulation. Nevertheless such solutions will never completely replace the.
The new Breach Attack Simulation real-world security verification method combines convenience with useful. Breach and attack simulations are an advanced computer security testing method. Gartner defines Breach attack Simulation BAS technologies as tools that allow enterprises to continually and consistently simulate the full attack cycle including insider threats lateral movement and data exfiltration against enterprise infrastructure using software agents virtual machines and other means.
Simulate sophisticated attack methods used by cyber criminals. Breach and Attack Simulation is a new way of testing IT security efforts that mimics real-world attack actions to determine if the companys various security measures actually serve their purpose. Breach and Attack Simulation BAS Products Compared Posted on April 14 2021 April 14 2021 by Balaji R 10 years ago when Gartner defined SIEM Security Information and Event Management it was trending in the cybersecurity landscape and every organization was looking for one.
With SafeBreach we can automatically execute attacks based on the specifics of the reported attack and determine if were exposed to the same risk. Overtaking manual periodic. Fully automated and customizable Attack simulation challenges your security controls against the full attack kill chain with thousands of simulated cyber-attacks both common and novel.
What Is Breach Attack Simulation BAS. These simulations identify vulnerabilities in security environments by mimicking the likely attack paths and techniques used by malicious actors.

 Breach And Attack Simulation Vs Penetration Testing Elasticito
Breach And Attack Simulation Vs Penetration Testing Elasticito
 Cymulate Breach And Attack Simulation Platform 3 30 16 Sc Media
Cymulate Breach And Attack Simulation Platform 3 30 16 Sc Media
 Breach And Attack Simulation Comprehensive Multi Vector Assessment
Breach And Attack Simulation Comprehensive Multi Vector Assessment
 Top Things To Consider In A Breach And Attack Simulation Platform Cyber Security Magazine
Top Things To Consider In A Breach And Attack Simulation Platform Cyber Security Magazine
 Open Source Breach And Attack Simulation Tool Infection Monkey Gets New Features Help Net Security
Open Source Breach And Attack Simulation Tool Infection Monkey Gets New Features Help Net Security
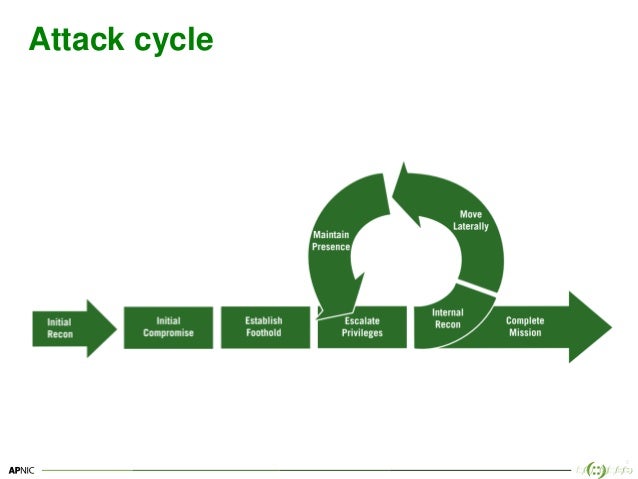 Breach And Attack Simulation Tools
Breach And Attack Simulation Tools
 5 Exciting Players In The Breach And Attack Simulation Bas Cyber Security Category Cyberdb
5 Exciting Players In The Breach And Attack Simulation Bas Cyber Security Category Cyberdb
Are You Apt Ready The Role Of Breach And Attack Simulation
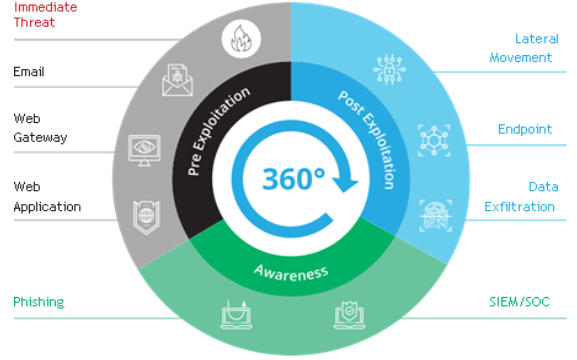 Breach And Attack Simulation Platform
Breach And Attack Simulation Platform
 Safebreach Brings Risk Metrics To Attack Simulation Platform Eweek
Safebreach Brings Risk Metrics To Attack Simulation Platform Eweek
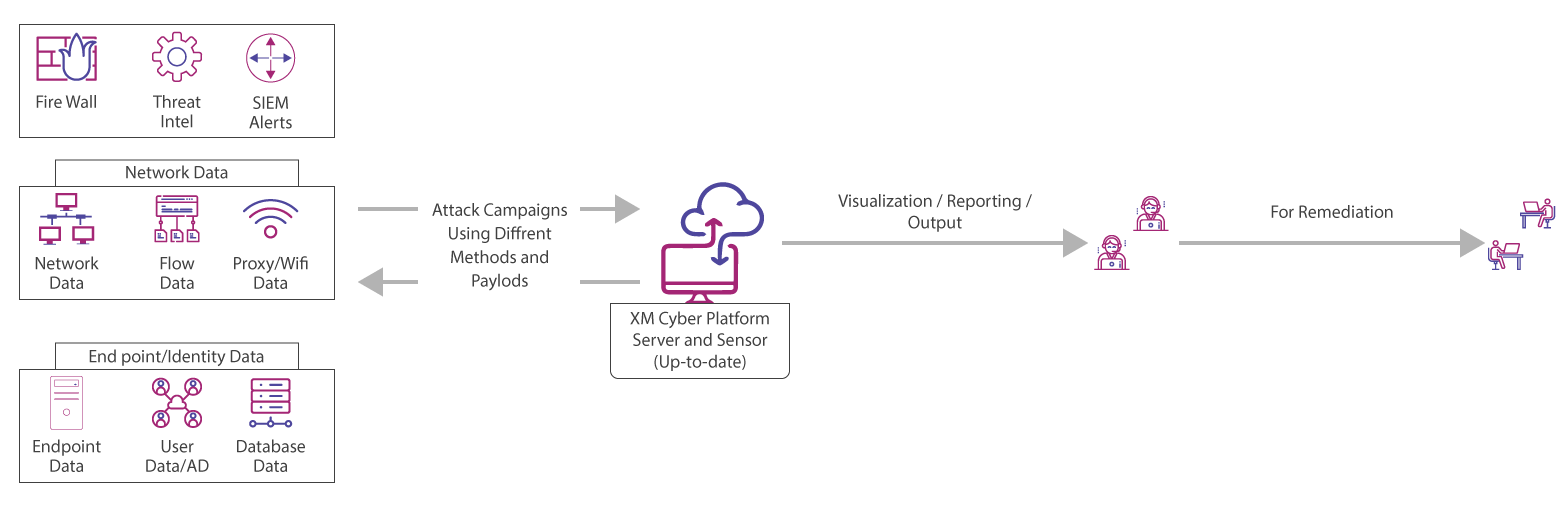 Cyber Attack Simulation Vulnerability Management Apt Mitigation
Cyber Attack Simulation Vulnerability Management Apt Mitigation
 How A Breach And Attack Simulation Bas Platform Can Help Financial Organizations To Be Better Protected The First Global Cybersecurity Observatory
How A Breach And Attack Simulation Bas Platform Can Help Financial Organizations To Be Better Protected The First Global Cybersecurity Observatory

No comments:
Post a Comment