It can run in a window as a separate computing environment often to run a different operating systemor even to function as the users entire computer experienceas is common on many peoples work computers. However this requires proper configuration of your VM on network level eg mode.
![]() Cara Mengaktifkan Teknologi Virtual Teknologi Intel Virtualisasi Apa Itu
Cara Mengaktifkan Teknologi Virtual Teknologi Intel Virtualisasi Apa Itu
301May 2005 Organization This volume begins with an overview of SVM followed by chapters that describe the following details of system programming.

Secure virtual machine. Azure Disk Encryption enables you to encrypt your virtual machine disks including the boot and the data disks. VM applications allow you to suspend the virtual machine. In Windows 10 Enterprise only in this edition a new Hyper-V component has appeared Virtual Secure Mode VSM.
Keeping a broad perspective of security and taking proactive steps to implement security improvements will go a long way toward keeping your valuable data safe and out of the wrong hands. Providing security recommendations for the virtual machines. Crucial from the security point of view system components run inside this protected virtual container.
VSM is a protected container virtual machine run on a hypervisor and separated from host Windows 10 host and its kernel. A key emphasis is on security by using as small a code base as possible making it. Service endpoints use public IP addresses.
To secure your virtual machines keep the guest operating systems patched and protect your environment just as you protect your physical machine. A Virtual Machine application allows you to avoid this by getting your VM fingerprinted instead of the host operating system. Enable Guest Virtual Secure Mode.
These logs need to be stored in your log vault for security and for auditing purposes at a later date. Consider disabling unnecessary functionality minimize the use of the. System ResourcesThe data structures system registers software responsibilities and hardware support to implement SVM systems.
Apply system updates configure ACLs endpoints enable antimalware enable network security groups and apply disk encryption. Credential Guard and Device Guard can protect a Hyper-V virtual machine just as it would on a physical machine. Ensure that any hardware you use is designed for VM usage.
Testing suspicious softwares and files. Virtual machines have become an important part of computing. Education is one of the best tools you have to secure virtual machines.
The diagram below illustrates the layers of security responsibilities. Azure Disk Encryption helps you address organisational security and compliance requirements by encrypting your virtual machine disks with keys and policies that you control in Azure Key Vault. Which is more secure.
Security Center helps you optimize and monitor the security of your virtual machines by. The answer will surprise you IBM Research has created a new way to measure software security Horizontal Attack. A virtual machine is a computer file typically called an image that behaves like an actual computer.
Strictly manage remote access to virtual machines and especially to the host machine this will make exposure less likely. In late 2019 Microsoft released Azure Bastion into General Availability. Security is a shared responsibility between Microsoft and the customer and as soon as you put just one virtual machine on Azure or any cloud you need to ensure you apply the right security controls.
Containers or virtual machines. Private endpoints are network interfaces that securely connect you to a service powered by Azure Private Link. Azure Rackspace IBM Softlayer and Oracle.
Monitor the event log and security events on both the host machine and on the virtual machine. Monitoring the state of your virtual machines. Secure virtual machines like physical machines and follow best practices discussed in this document and in the Security Configuration Guide formerly known as the Hardening Guide.
Private endpoint uses a private IP address from your VNet effectively bringing the service into your. Secure Virtual Machine Architecture Reference Manual 33047Rev. Azure Bastion provisions directly in your Azure Virtual Network acting like a jump server as-a-service.
The guest operating system that runs in the virtual machine is subject to the same security risks as a physical system. It is a new fully platform-managed PaaS service which provides secure and seamless RDPSSH connectivity to your virtual machines directly in the Azure portal over SSL. NAT with no port forwarding Internal network to avoid any leakage of host operating system attributes eg hostname IP.
Once you enable service endpoints in your virtual network you can add a virtual network rule to secure the Azure service resources to your virtual network. But before you enable Virtual Secure Mode in a virtual machine there are certain requirements that you have to be aware of. Stay current on vulnerabilities not only pertaining to VMware but to all the levels in your environment.
 Proposed Architecture For Secure Migration Of Virtual Machine Download Scientific Diagram
Proposed Architecture For Secure Migration Of Virtual Machine Download Scientific Diagram
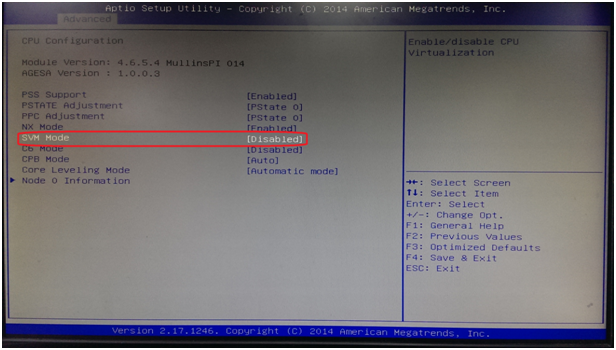 Pejuang It Cara Mengaktifkan Intel Virtualization Technology Dan Amd Secure Virtual Machine
Pejuang It Cara Mengaktifkan Intel Virtualization Technology Dan Amd Secure Virtual Machine
 Thoughts From The Uk Amd Svm Secure Virtual Machine
Thoughts From The Uk Amd Svm Secure Virtual Machine
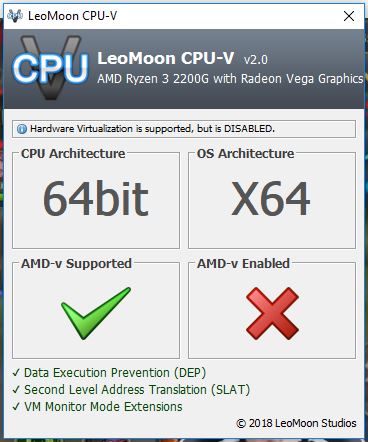 Cara Mengaktifkan Secure Virtual Machine Amd V Pada Prosesor Amd Teknosid
Cara Mengaktifkan Secure Virtual Machine Amd V Pada Prosesor Amd Teknosid
Part 7 Creating Nested Vmware Esxi Server Vm In Home Lab On Vmware Workstation Vgeek Tales From Real It System Administration Environment
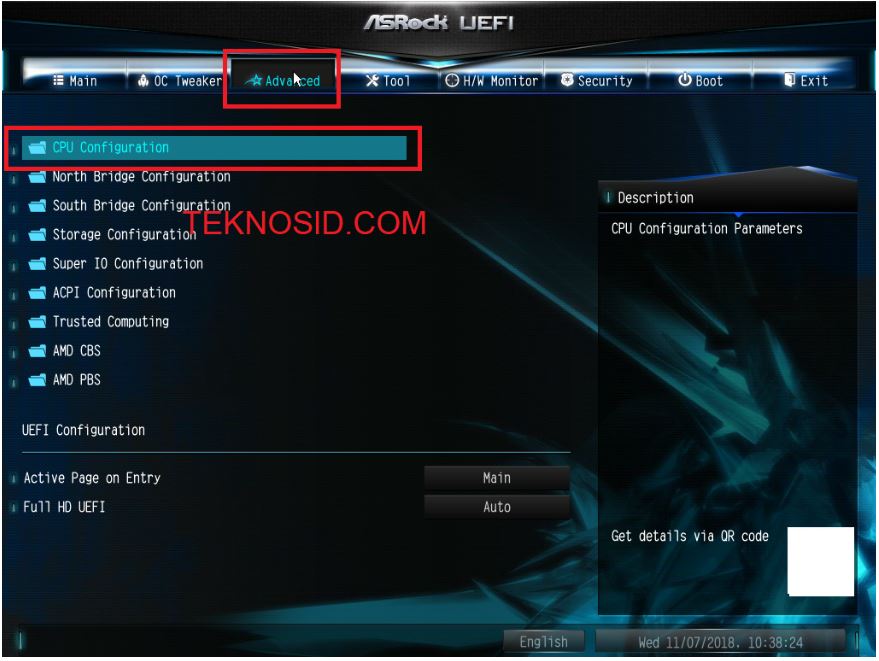 Cara Mengaktifkan Secure Virtual Machine Amd V Pada Prosesor Amd Teknosid
Cara Mengaktifkan Secure Virtual Machine Amd V Pada Prosesor Amd Teknosid
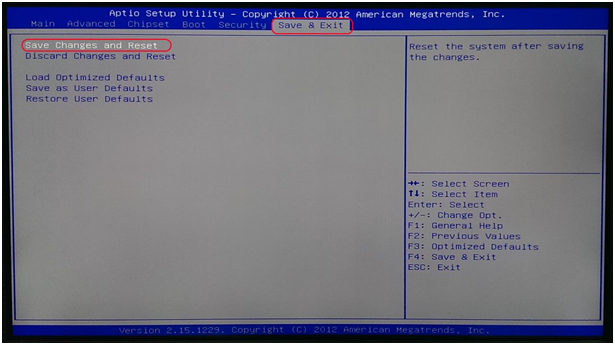 Pejuang It Cara Mengaktifkan Intel Virtualization Technology Dan Amd Secure Virtual Machine
Pejuang It Cara Mengaktifkan Intel Virtualization Technology Dan Amd Secure Virtual Machine
 Pulse Secure Sa Series Ssl Vpn Virtual Appliances Secureaccessworks Com
Pulse Secure Sa Series Ssl Vpn Virtual Appliances Secureaccessworks Com
 How To Enable Intel Vtx And Amd Svm Qnap
How To Enable Intel Vtx And Amd Svm Qnap
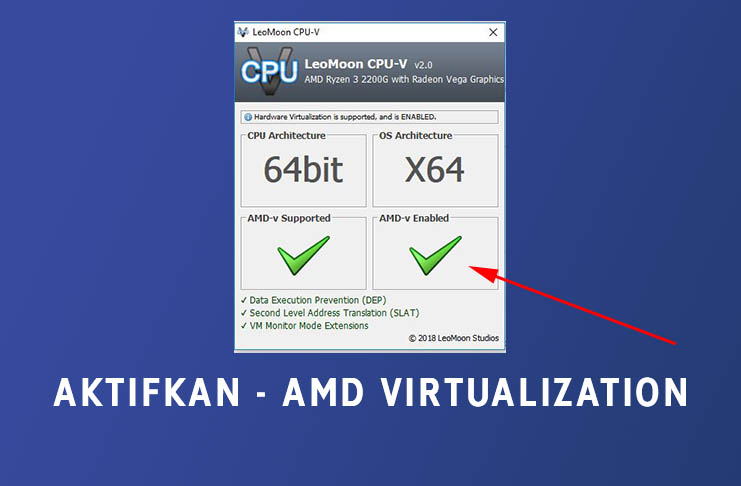 Cara Mengaktifkan Secure Virtual Machine Amd V Pada Prosesor Amd Teknosid
Cara Mengaktifkan Secure Virtual Machine Amd V Pada Prosesor Amd Teknosid
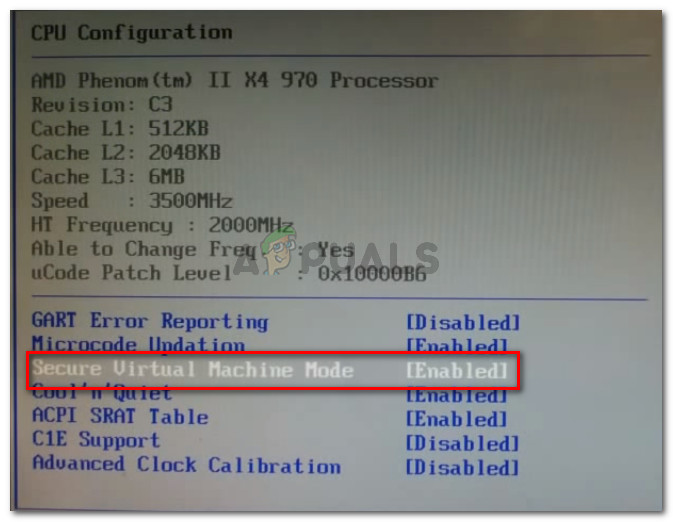 Fix Amd V Is Disabled In The Bios Verr Svm Disabled Appuals Com
Fix Amd V Is Disabled In The Bios Verr Svm Disabled Appuals Com
 Protected Storage A User In Secure Virtual Machine Vm Can Access The Download Scientific Diagram
Protected Storage A User In Secure Virtual Machine Vm Can Access The Download Scientific Diagram
 How To Enable Intel Vtx And Amd Svm Qnap
How To Enable Intel Vtx And Amd Svm Qnap
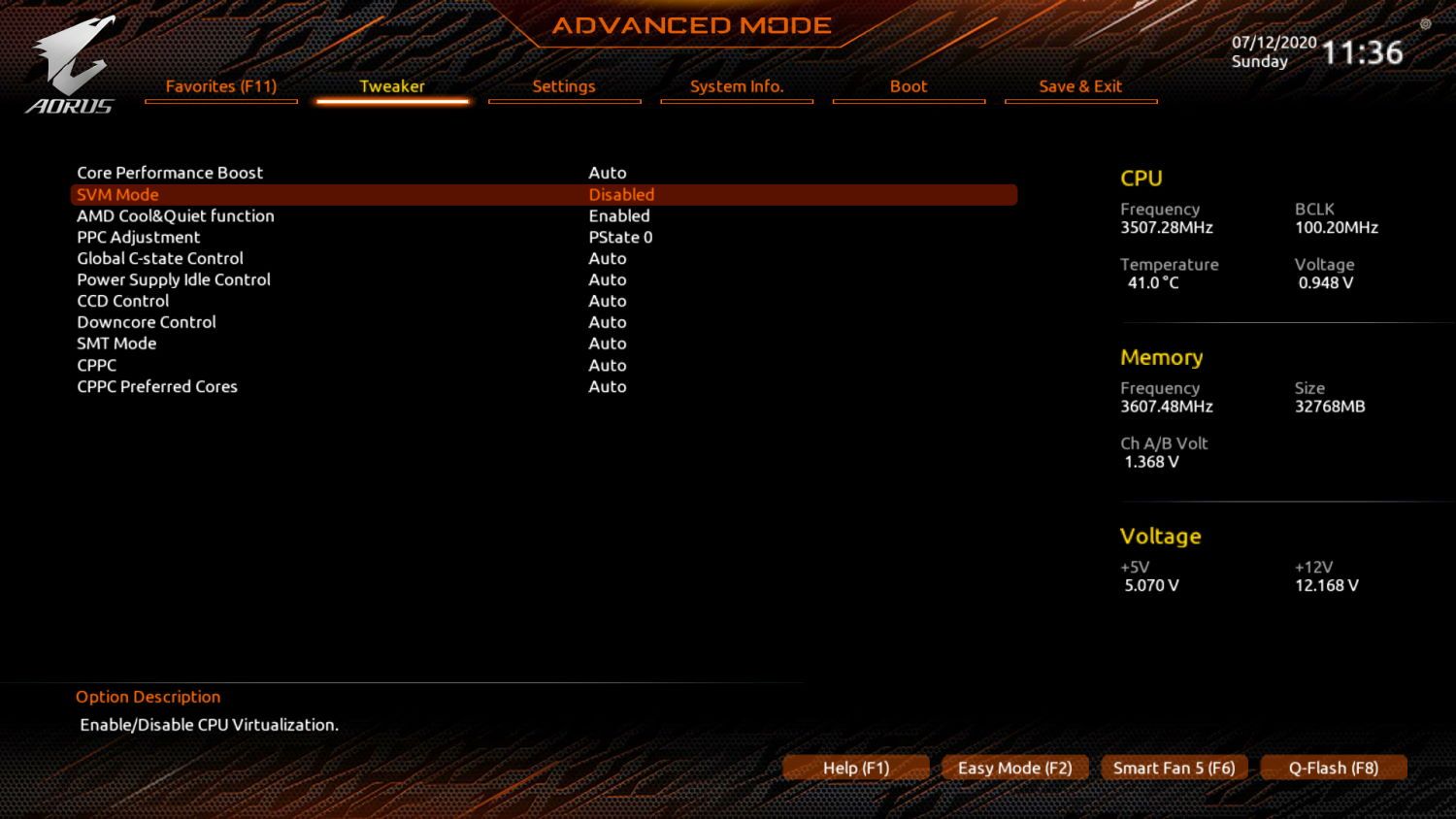 How To Enable Amd Virtualization On The Aorus X570 Motherboard Our Code World
How To Enable Amd Virtualization On The Aorus X570 Motherboard Our Code World
No comments:
Post a Comment